
Financial Services Guide: Managing Technology Risk With NIST
A Guide for Financial Services and Regulated Firms
Dealing with risk is complex, and that level of complexity tends to escalate when addressing technology risk. Most people, including experienced risk managers, feel intimidated by the amount of technical detail involved. After hearing the concerns of many customers and partners, we decided to put together this guide on how we succeed in the challenge of managing technology risk.
Today you will learn of a framework and a set of tools that will make the task of addressing technology risk feel achievable. By leveraging the NIST framework, you can build a Risk Management system that will allow your business to reach top-level security and compliance. Plus, the best part: it’s easy to understand and verify progress.
We will be explaining what NIST is, how it works, and how you can begin implementing it in your organisation. The benefits are evident for companies in the Financial Services industries or for most businesses that operate in highly regulated spaces. However, the advantages of a robust risk management system and a cyber security framework are universal and will help all types of businesses thrive among today’s threats.
Click on the links below if you want to skip to any particular chapter and follow the links within them to dive further into more detail.
Understanding IT Cyber Security Risk
By now, businesses across the globe know that their IT infrastructure is at risk from attacks or breaches from cyber criminals, no matter how large or small they are, or what they offer.
For financial services organisations, it’s even more important to be aware of the risks and to come up with a plan to prevent and resolve any issues arising from an attack. When you hold a client’s financial information or provide a platform for people to save and move money, you want to ensure that that plan is as robust as possible.
It’s important, however, to understand first that there is no such thing as perfection in cyber security, and risk management is not a race, it’s an ongoing process of improvement.
Knowing that risk is something you’re always going to have to deal with means that you can regard it as an opportunity and allows you to be proactive in your approach to data protection and security. You don’t need to be an expert technician to avoid IT risk – it’s all a matter of asking the right questions.
In order to protect your business and its data (as well as that of clients and suppliers) and to ensure you’re compliant with financial regulations, you need to build a cyber security framework.

NIST is one of a number of frameworks, but it’s simple to understand and can be adjusted and applied to the IT systems of any company, no matter what their size. The business can then develop a cyber security system entirely tailored to their needs.
Still not sure about the usefulness of a framework? Read the following article:
Understanding Guidelines, Frameworks and Standards (from a Governance Standpoint)
NIST starts with a basic assessment of where a company is and where it wants to be. Understanding the difference between the current and desired state should help companies to carry out a gap analysis, to define their target risk profile and produce a risk assessment.
It’s important that careful consideration is given to the threats and vulnerabilities specific to financial organisations.
What is NIST?
The National Institute of Standards and Technology (NIST) has developed a Cyber Security Framework which they define as: “a policy framework of computer security guidance for how private sector organizations can assess and improve their ability to prevent, detect, and respond to cyber attacks.”
Once the assessment process is complete, NIST provides a risk-based action plan and cyber security insights that are appropriate for both board and executive-level review and implementation. The information generated is also easily quantifiable.
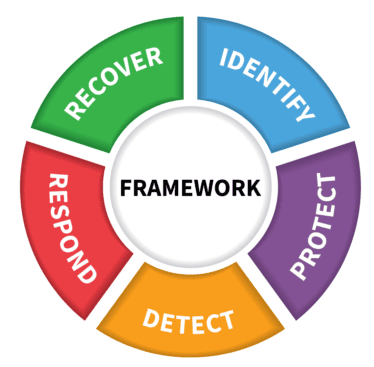
The NIST process is made up of three stages, each building upon the other to help a business to assess its current systems and draw up a plan. It includes five functional areas to consider: Identify, Protect, Detect, Respond and Recover. We will dive into more detail on these areas shortly.
How can NIST Help Financial Services Organisations?
The NIST Framework helps companies to: ‘better understand, manage, and reduce their cybersecurity risks’. Completing the assessment means you can identify your individual priorities when it comes to cyber security and business continuity.
NIST is internationally recognised and designed to be shared with all employees, as well as with suppliers. Rather than making cyber security the responsibility of the IT department alone, the framework helps senior managers to communicate the importance of keeping data safe.
It also helps you to stay GDPR compliant. Since the legislation was introduced in 2018, all companies holding customer data must be proactive about how they safely store and remove that information. Anyone who falls foul of the regulator faces large fines.
Going through the process helps you to assess your current IT systems and allows you to fix any gaps, reducing your chances of data being compromised. It also means that if anything does go wrong, you’re prepared for it and can implement your continuity plan.
For more in-depth information about the NIST CSF, visit the official website or ask us in the comments section at the end of this page.
Applying the Framework
As we mentioned above, the NIST Cyber Security Framework is comprised of three sections. To help you get started, here is a quick explanation of what each of these is and how they fit in.
The Framework Core
The Core is designed to give you tasks to work through to help you reach the cyber security outcomes that you’ve identified as being necessary for your business. Within the Core, you can add references to where readers can find additional information on best practices, procedures and industry requirements.
The Core is written in clear, straightforward language so that it can be easily understood by anyone at any level within the organisation and doesn’t require a knowledge of technical jargon.
To make it easier to assess your needs, the Framework Core is spit into five functions, as mentioned above, which are: Identify, Protect, Detect, Respond and Recover. NIST recommends using all five together for a ‘high-level, strategic view of the lifecycle of an organization’s management of cybersecurity risk’.
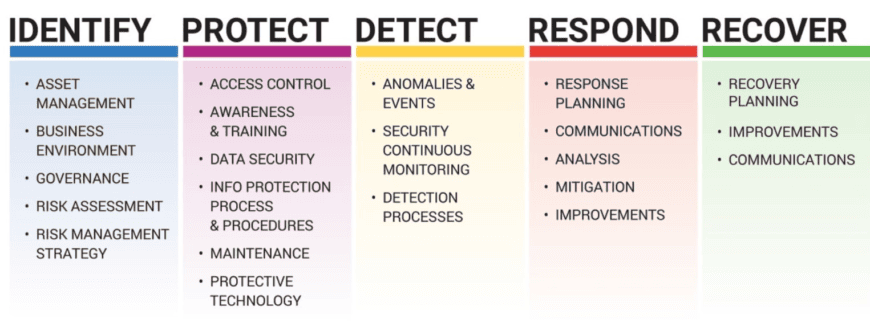
Identify: The first step is to get an overall picture of the business, the resources available to support critical functions and the potential risks to data, assets and systems. Once these risks have been identified, you will then be able to create a strategy for use throughout the business to prioritise and manage them appropriately. Things to consider at this step include governance, the business environment and asset management.
Protect: The next step is to develop safeguards to make sure your company can deliver critical services. NIST suggests giving thought to data security, protective technologies, access control, awareness and training and identity management. Also include an implementation plan for the safeguards.
Detect: This function is designed to help you detect cyber security events in a timely manner and develop processes to do so effectively. It’s recommended that you include continual monitoring of systems and security, as well as how to identify anomalies or other changes.
Respond: NIST says that this function is intended to make sure you have the ability to contain the impact of a cyber security incident, should one happen. Take into account response planning and communication, as well as what to do afterwards, including analysis of the incident, mitigation and possible improvements that you can make to prevent an attack in future.
Recover: At this step, you’re working to map out your recovery plan and the improvements you’ll make for the future, as well as identifying how you’ll communicate this across the organisation. The key priorities here are to be able to get back to normal operations as quickly as possible in the event of a cyber attack and how to restore any services that were affected during the attack. Business resilience is important at this stage.
Within the Framework Core are underlying key Categories and Subcategories (outcomes). There are 23 Categories which are mapped against each of the five Functions outlined above. These include suggestions for cyber security objectives, such as personnel education. Think of them as brief topics you can include to help you reach your business outcomes.
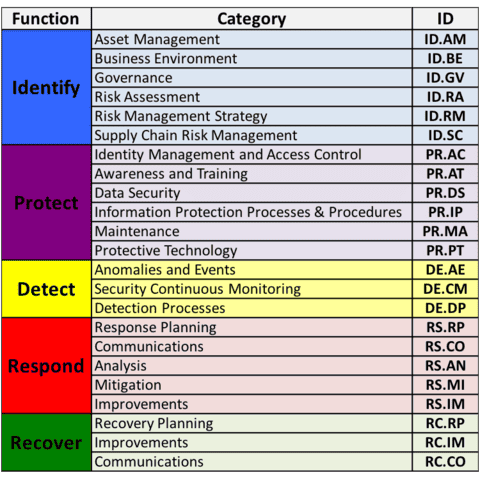
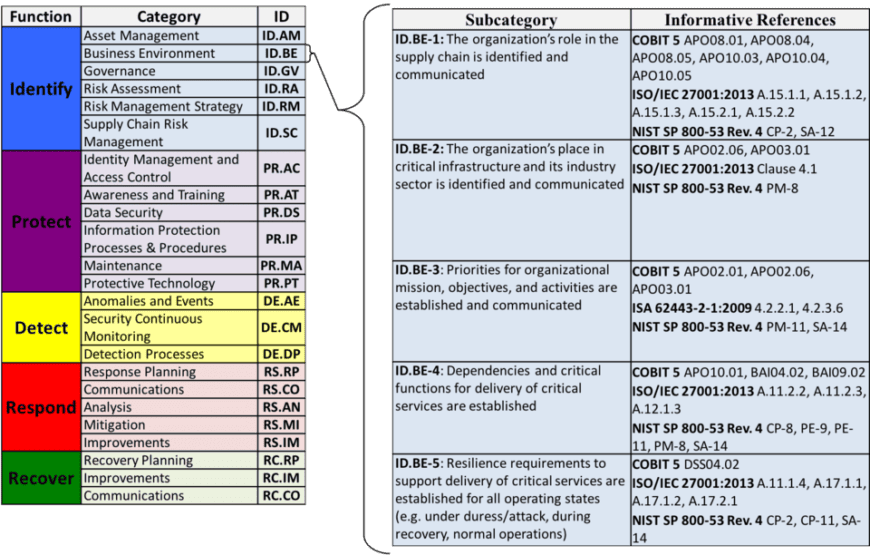
Next, there are 108 Subcategories, which NIST describes as: “outcome-driven statements that provide considerations for creating or improving a cybersecurity programme”. These can be amended to suit your own requirements.
NIST Framework Implementation Tiers
The next section of the Framework covers the Implementation Tiers. The four tiers assess how an organisation views cyber security risk and what processes it has in place to manage that risk. The Tiers are used to decide how a business is prepared for and will respond to a cyber breach or attack.
- Tier 1 – Partial Implementation: At this level, businesses have minimal awareness of the risks they face. Planning and implementation is inconsistent, and they take an ad-hoc and reactive approach to cyber security.
- Tier 2 – Risk-Informed: Here, companies are aware of the need for cybersecurity measures and have some idea for what these should be, but aren’t implementing them regularly. While they have plans and resources to protect themselves, they aren’t proactive.
- Tier 3 – Repeatable: This tier refers to companies which have implemented the Cybersecurity Framework across the board, apply policies consistently and communicate fully with employees at all levels so they understand the potential risks and the steps to take. The word ‘repeatable’ means that the business is able to respond to more than one crisis that may occur.
- Tier 4 – Adaptive: At the final stage, businesses have fully integrated the Cybersecurity Framework into their processes. Not only are they equipped to respond to and deal with threats, they are proactive with detecting them. They can also predict any issues based on the IT systems they have in place and any current trends.
Further below, we will provide a simplified tool to help you evaluate your current practices and understand where your business stands among these Tiers. It’s helpful to know that they don’t necessarily reflect your business maturity (although if you’re at Tier 1, moving up is recommended).
Instead, the Tiers should be seen as a way to help you manage risk, your priorities and how you can improve cyber security and progress to the next level at the right time for your company. They help you move from being reactive to proactive in terms of responding to risk.
As for your target profile, choose a Tier that reflects your desired outcomes and is achievable. You must select the appropriate Tier considering your ideal risk management practices, any legislation and industry regulation requirements (essential for financial services) as well as any obligations you have to others in your supply chain and any constraints that may exist.
NIST Framework Profile
The final stage is the creation of a Profile which is unique to your business. It is based on your objectives and requirements, the level of risk and the priorities you identified at the Core stage. It’s built using the Categories and Subcategories that you’ve chosen as being important to help you build a robust cybersecurity plan.
One advantage of spending some time developing a Profile means that, once you’ve assessed where you are now (Current Profile) you can start looking for ways to improve your cybersecurity and move to where you’d like to be (Target Profile).
Any gaps between Current and Target Profiles mean you can develop a plan to resolve them, based on what’s most important and time-critical to ensure your systems are protected.
Within this, factor in any other business needs, such as staffing and resources, costs, future planning and overall goals and other outside influences (such as changes to legislation or technology). Plan how to communicate the Profile and the goals to internal staff and external suppliers.
Learn where you are – Estimate your current NIST Profile
To get you started, we have developed a simplified self-assessment tool that you can use to evaluate your business and identify your current and target profile. By using this tool, you should be able to have a better practical understanding of how useful NIST can be. Keep in mind that it doesn’t cover all bases normally addressed by the framework, especially since we have shifted it from a levelled approach (1-4) into a “yes or no” approach to keep things simple.
Download the NIST CSF Simplified Self-Assessment Tool
Watch the video below for a detailed explanation about how to estimate your NIST profile and use the tool.
Strategy and Delivery to Implement the NIST CSF
The NIST Cyber Security Framework will then allow you to move on to analysis and planning and delivering your strategy. At this stage, you are working to identify your target (ideal) cyber security system and assess the current situation to see where there are gaps and what your business needs to do to hit the target.
Remember, completing the NIST Cybersecurity Framework is not enough on its own. While it will help you think through your security needs, you need to decide what steps to take next.
Once you’ve clarified your current cyber security position, your Target Profile (see above), identified any gaps and decided how to resolve these, you can move on to putting together your plan.
Don’t forget to include any legal requirements (such as GDPR) and industry regulations you may need to consider. Here are some other things you’ll need to think about:
Complete a Detailed Asset Register
An asset register (sometimes called a fix asset register) is a record of every fixed asset you have in your business – anything that you use to generate revenue. It includes computers and other devices, vehicles, machinery and equipment, buildings and land.
You can record and track your assets however you wish, but an electronic list in a spreadsheet or similar is ideal because you can share it across teams or department heads who need to be able to access and update it.
It’s also important to review your asset register and keep it current, so allocate a regular time to review it, whether that’s quarterly or six-monthly. The register tracks the value of all the fixed assets within the business, if it works, and its location. You’ll need to work out asset depreciation at the end of each financial year too.
It’s up to you what information you include on your asset register, but at the minimum, note its name or give it a description so you know which item you’re talking about. Include serial numbers or other identifying numbers.

Add how much each asset was bought for and when and its original purchase price, the depreciation and current book value. You might want to include service history or if it’s a vehicle, if it’s been repaired/ or last had an MOT.
Assign an owner to each asset, and where appropriate, allocate a risk weighting. A risk weighting is essential for banks, as it enables a calculation to determine its capital requirement and to reduce the risk of insolvency. Different classes of assets have different risk weightings applied to them, as some are riskier than others.
Depending on the asset, its risk will be assessed using the most appropriate tool. A calculation should also be done to calculate interest that may be charged, and the rate of return.
For more detail and practical examples of how to build your Asset and Risk Register,
read our article: Building an Asset and Risk Register to tackle risk
Building a Risk Register
A risk register is a way of plotting the impact of any given risk over its probability. A scatterplot is the usual method of presenting the results, with impact across the X-axis and the likelihood of it happening on the Y-axis. The risks are then all marked on the graph. You can also use specialist software to track the risks.
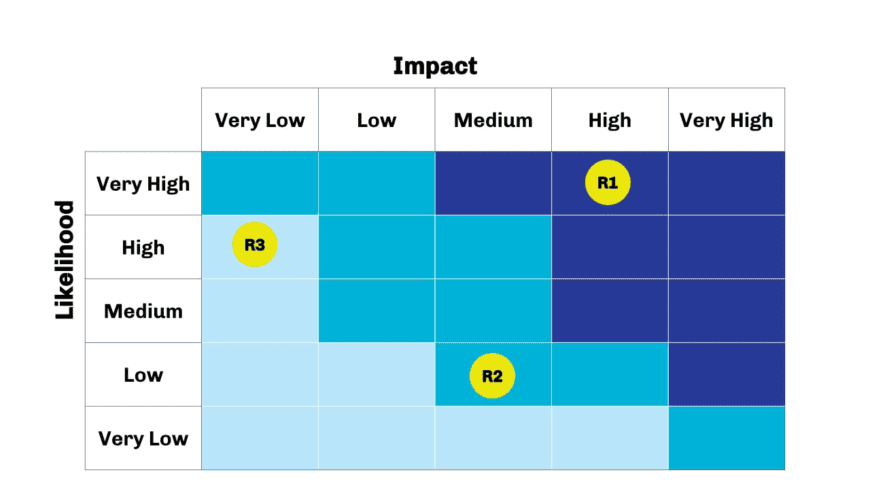
The register also includes any other relevant information about each risk, such as its owner, the nature of the risk, and what, if any, mitigation measures are in place, and any contingency plans. It also discusses what impact a risk will have, and how likely (probable) it is that the risk will happen. Similar risks can be grouped together.
To help you visualise and build your risk register, we have acquired a Sample Risk Register and made a video with instructions and practical tips on how to insert and organise your risks onto the spreadsheet. You can access both below:
Watch our Web Class below on how to complete your Risk Register
Set an Action Plan to Address Technology Risk
The information you’ve gathered while completing the NIST Cyber Security Framework should clearly show what your next steps are. Decide and agree on the actions the business needs to take across the next 12 to 24 months.
Set milestones for when you’ll change or update your security systems, how and when you’ll move from your Current to your Target Profile, and how you’ll track your progress. Include review dates for each step, and make sure you clearly communicate the plan and how it’s progressing with everyone within the organisation.
Knowing how to address your main risks is also crucial in improving your business profile, and there are different ways to do it, depending on your budget and priorities. For example, a risk can be tackled straight on, it can be outsourced, insured or even ignored. Everything depends on how significant the risk’s impact, costs and probability are, and all these factors should be considered when preparing your Risk Register.
For more information on how to build your action plan and address risk, read:
Developing an Action Plan to Address your Technology Risk
Collecting and Storing Evidence of Compliance
A crucial, yet commonly unappreciated, part of this process is to gather and store evidence of your activities along the way. To be compliant, you must be able to prove that you are compliant. This is where the evidence-gathering process begins, and it should function in parallel with your efforts to tackle risk.
There is a multitude of procedures, policies, systems and tasks that support this effort. We recommend utilising tools and specialised services to make this process automatic and as easy as possible.
The key take away from this chapter is that it supports the next stage – The Audit process. By maintaining this evidence, you can decidedly prove to an auditor that your business has been compliant with best practices and takes this task seriously.
For more information and details on the tools and methods we recommend, read:
Before the Audit: Gathering Evidence to Prove Compliance
Develop the Risk Management System
Next, you’ll need to develop your risk management system. The system will not only advance your technology infrastructure but will allow your organisation to improve in other key business areas and evolve in maturity. The company will run like a well-oiled engine, with processes and procedures supporting activities.
Below, we explain how the NIST Cyber Security Framework can assist in developing some of these areas.
Governance
Most government requirements are covered in the ‘Identify’ function, which is stage one of the Framework Core. Other requirements will come under the relevant headings, such as ‘detect and respond.’
Cyber Security
Cyber security is tracked across all five of the Core areas, with the main controls included in Protect and Detect. It’s a good idea to take into consideration the CIS 20 controls.
The Centre for Internet Security Critical Security Controls for Effective Cyber Defence is a guide to best practice for computer security. It consists of 20 key actions which serve as guidelines for organisations to take to block attacks. and are known as critical security controls (CSC).
Business Continuity Plan (BCP)
This is covered across all functions, particularly the Recover function. A BCP is essential for all businesses, but particularly for financial institutions. Having a robust continuity plan in place means you can be prepared in case the worst happens.
It means you can continue with business as usual while data is restored or cyber threats are dealt with, enables you to communicate with your customers, staff and suppliers and ensures that everyone knows what to do to help the business operate properly.
Outsourcing
Is covered within the Identify function and falls under the category of Supply Chain Risk Management. It’s essential that if you are part of a supply chain, your business is not vulnerable to external risks which could compromise not only your systems but those of everyone else in the chain too.
If you decide to purchase new technology, make sure it’s compatible with your existing hardware and software, it can be secured against data breaches and that it’s installed by the in-house IT team or your external support partner.
For more insight on outsourcing, read: Outsourcing Policy – Governance, Risks and Preparations to consider

ISO Standards
As with other aspects of business, ISO standards apply to cyber security frameworks, although of course these vary depending on industry. ISO 27001 is a general standard for Information Security Management Systems and sets out explicitly how this should be controlled.
ISO 27002 includes the BS 7799 good security management practice standard, which outlines the best practice for cyber security management, and operates as a high-level guide. It’s most helpful to use it as guidance for management looking to achieve ISO 27001 certification.
For financial institutions, having ISO 27001 certification is hugely beneficial. As they hold so much personal and financial information on clients, often across devices and locations, they are particularly at risk from cyber-attacks.
Holding the ISO certification demonstrates to customers that the institution is committed to security, confidentiality and protecting their data, and are proactive in doing so. In the post-GDPR world, this is more important than it’s ever been and will help you stand out from the competition.
ISO 27001 and the NIST Cyber Security Framework have many similarities and overarching areas. This is a good thing, as if you are looking to adopt the framework or achieve the certification, you can transition from one to the other without dissipating your efforts. To learn more about which of these models can be more beneficial to your business, read our article ISO 27001 versus NIST: why choose one?
Preparing for an Audit
Financial Services organisations and companies operating within regulated industries are familiarised – and often terrified – with the concept of an audit. Utilising NIST and a risk management system, this process should become much more straightforward and painless.
An audit is a vital process for identifying fundamental weaknesses in your company’s formal procedures or cybersecurity architecture. It is not a name and shame process; audits exist to help you grow. Internal audits could potentially be just as effective, but the added pressure from an external auditor is what usually closes the gap between an organisation’s plans and actions.
However, as relevant as cybersecurity audits are, many companies are not very well prepared for them. Learning what do you need and how to behave in a review will bring more peace and efficiency to the procedure. The critical lessons are:
Communicate with the auditor: Speak to the auditor before and during the process, so you can both be as clear as possible on what is needed. Know the scope of the inspection, and what people, tools and reports will be required to have them available when requested.
Prepare in advance: The more time you prepare for this process, the less time the auditor will need to be in your site. Study up on the applicable regulatory standards prior to the audit, prepare your files and docs in an easy to read format, and be ready to show a register of your assets.
Don’t be afraid: the auditor is not your enemy, and the sole fact of changing your perspective towards this figure may show some significant improvement in your relation and process. Ask him to let you know of any significant issues as they arise, and be sure to ask for advice, as your problems will likely not be exclusive to you and there might be simple solutions available.
For more in-depth insights on being audit-ready, read:
Preparing for an Audit: How to tackle Cyber Security and discuss it with the board

Dealing with the Board
Apart from dealing with the auditor, it’s equally important to report progress to the board and make sure that the goals and actions to attain these goals are fully understood and supported by them.
Educating the board about the relevance and role of the tech infrastructure of your business is an excellent place to start. It would be best if you also kept things as simple as possible, as this will likely be only one amongst many items in a list to be discussed by the board members.
One of the main advantages of the NIST framework is that it can demonstrate progress with its uncomplicated ranking system. Any non-technical person or board member should understand and learn about what are the most critical areas.
We talk about the guiding principles for board reports, as well as some of the key questions to help identify and develop cyber security metrics in this article.
Maintaining the Risk Management System
As we said at the beginning, cyber security is not a once-off event; it is an ongoing process which needs to be continually monitored and improved. It’s not something that you can set and forget or leave to the IT department to manage.
Regular reviews of the systems in place using the NIST Framework should be agreed amongst the senior management team. Track examples of best practice and highlight areas for improvement, and make sure you communicate the results with the rest of the organisation.
The system can be maintained and handled by yourself, with enough discipline and by utilising calendaring tools. In this case, you will retain all of the documentation, evidence gathering and calendaring of reviews (such as backup tests, incident management etc.) using a centralised document management solution such as Sharepoint or Microsoft Teams.
However, depending on the size or complexity of your organisation, we would recommend hiring a specialised solution to facilitate this process. It will need to support the NIST Cyber Security Framework and provide you with the outputs that you need.
There are some excellent Integrated Governance, Risk and Compliance tools out there, all with their own strong points. At the very minimum, it needs to manage the tasks, repeat reviews, document and evidence gathering as well as provide detailed and executive progress reporting.
It makes the whole process from Vendor evaluations to day to day tasks management and compliance control way simpler.
If you consider specialists’ help and tool, you must understand the value it will bring to your business. Being secure against threats, audits, and with a future-proof structure and strategy that fits your business’ unique characteristics are the outcomes that you seek. Depending on how much knowledge you have obtained about your tech infrastructure structure, we are able to suggest an appropriate solution.

How Can We Help – Implementing NIST into your Business
Here at Spector, we have two basic service offerings in this area: the Gap Analysis and the Cyber Security Programme.
We usually recommend companies to begin with the Gap Analysis, as it will provide us with more knowledge of your setup and a clear direction for your needs. This service consists of a project to analyse and identify the most critical vulnerabilities in your structure. It can be done in a short period by our team, causing minimal disruption. To learn more about how it works and what is involved, read our Gap Analysis brochure, available on this link.
The Cyber Security Programme, on the other hand, is the following step after the Gap Analysis, and it will address the actual mitigation of your risks and development of your structure on a continuous basis. We will lay our tools and resolve the most urgent issues, to then initiate new projects to reach your business goals. This allows us to close the gap between desired and current state. If you want to learn more about this stage, we have information available on this link.
Both solutions will help turn this daunting process into an automatic and uncomplicated job. If you have questions, feel free to Book a Call with us. We will be happy to learn about your challenges and figure the best solution.
Thank you for reading! If you have found value in this content, please share it with others who may feel the same way. Follow us on Social Media for more exclusive content.

