
How Does Identity Theft Happen?
Estimated Reading Time: 5 Minutes
Hopefully, you have already read part one of this series of blog posts on identity theft. Following on from the initial post which gave a primer on identity theft, this second part covers how identity theft is perpetrated.
Identity Theft is a Prolific Cyber Crime
Before jumping into the meat of this post, take a look over some of these facts, they demonstrate very clearly that identify theft and cybercrime in general, is a major issue, and one that is trending upwards.
A recent survey undertaken by Eurobarometer in Ireland demonstrated that a third of the 1,000 people who took part, had been the victims of some form of malware attack. Further facts uncovered included:
- 13% indicated that they had lost out financially to some form of online scam.
- 57% confirmed that they often open emails from people who they do not know.
- 26% of them change their password at regular intervals.
- 75% use the same password for multiple websites.
- 10% had been the victim of credit/debit card fraud or a similar crime.
And when it comes to identity theft, 9% of the people who took part had been the victim of this cybercrime. This is almost 1 in 10 people.
How Your Online Identity is Exposed to Risk
All cases of identity theft share one common similarity. That the cybercriminal was able to gain access to some critical piece of personal information, which allows them to begin the process of stealing an identity. There are many ways that we expose our own personal data to the risk of loss, including:
- Theft or loss of a wallet or purse – that contained personal documents such as driving license and credit/debit cards.
- Theft or loss of a device – such as a tablet, laptop or smartphone, on which the owner has stored critical private data.
- Stolen snail mail – containing documents such as credit card or bank statements, tax information or letters with personal data.
- Dumpster diving – whereby a criminal goes through the garbage a person has thrown out looking for documents containing critical data (again, such as credit card or bank statements and tax information)
In most occasions, however, a criminal doesn’t need to physically act to steal an identity. There are many alternatives for that in the digital environment that facilitate this activity, such as:
- Insecure network connections – that are not secured behind a firewall or are vulnerable to some form of cyber attack.
- No enforced strict password policy – allowing users of a website to create passwords that are weak and easily cracked using the brute force method or are easily guessed. We have an article with insights on how to create and manage stronger passwords here.
- Being phished – when a user falls for a phishing scam, and inadvertently gives their own personal data away. Learn how to identify a phishing attempt and train your staff to avoid this threat.
- Corporate data leaks – a number of organisations today probably maintain records that include your personal information and bank or card details. If the company fails in their duty to keep this data secure you could be exposed to risk.
Of course, there are far more risks than these we have covered above; these are simply the most common.

You don’t need any special skills, or even much technical knowledge to steal a person’s online identity. All it takes are basic Internet skills and a lot of patience. Depending on the target, it could be done in less than an hour.
Identity theft begins with a fact-finding mission. The cybercriminal will try and learn as many facts about the victim as they can. This is shockingly easy to do. Sites such as Facebook and Twitter can provide information such as the names of family members and pets, the bank you use, where you work, the significant dates in your life (birthdays, anniversaries, etc.), your favourite restaurants, the kind of TV shows you like, and the list could go on and on.
Other sites, such as those that provide a database of criminal offences, county court judgements and even bankruptcies can also provide good data.
Simply plugging a person’s name into a Google search can often bring back masses of information about a person, especially if they are a prolific blogger, or maintain active profiles on services such as Spotify.
Once the cybercriminal has enough information about you, they then have many options open to them. They can use the information to try and gain access to services such as Gmail. How many sites ask us to set security questions such as, “What was the name of your first pet?”, “What was your Mother’s maiden name?”, or “What was the name of your first school?”. It is very simple to see how a person, knowing the kind of information about a person that would be used to answer these questions, can very easily gain access to such services.
Another option is that the cybercriminal can use the information that they know about you, to try and gain information in another way. For example, if an identity thief were trying to gain access to your online banking. If they know enough about you, they could call your bank, and do a sufficient job of convincing the people on the other end of the phone that they are you.
The Enabling Technologies of Identity Theft
All a cybercriminal needs to carry out identity theft is a computer/laptop and an Internet connection. No special devices or specialised software is used at all. That’s not to say that a well-rounded cybercriminal won’t have tools at their disposal that they use for other purposes, which could help with identity theft. Tools such as a network packet sniffer, or a brute force password hacking application.
No discussion of identity theft would be complete without mentioning the Dark Web. This is a hidden, private network of websites that are not typically accessible unless you know exactly where to find them. They don’t appear in search engines, and they work in a slightly different way to standard sites.
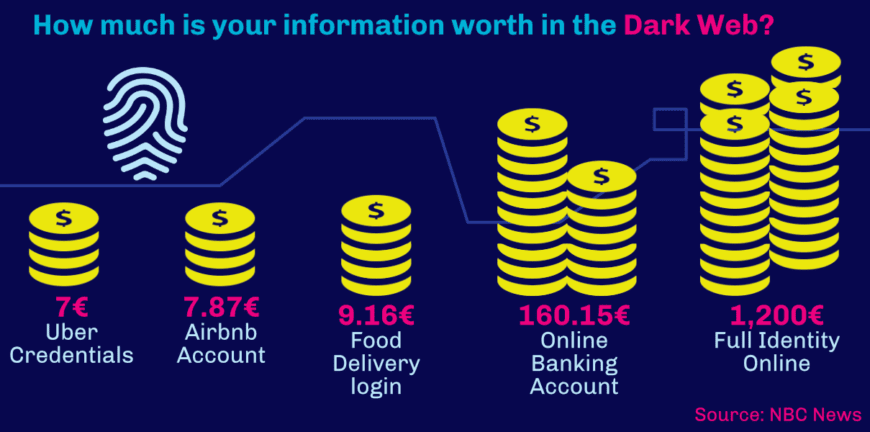
The Dark Web is the wild west of the Internet, with no policing or moderation. It has been used for everything from dealing drugs to hiring a hitman. A massive amount of information of interest to identity thieves is available for free, or for trade on the Dark Web. This is also where identity thieves sell identities that they have already stolen. Criminals pay an average of $160.15 to obtain an online banking account, and they can access other accounts for much cheaper according to this article by NBC News.
Curious about how much is your information worth out there? Check the graph below:
In Conclusion
This second part of our series on identity theft has hopefully demonstrated how shockingly simple it can be to steal a person’s identity, even if they have taken steps to protect it. The take away here should be that although there are things you can do to protect your own digital identity, we all rely on multiple third-parties to “keep their end of the bargain” and make sure they store our critical data securely. One layer of security is not enough and has to be reinforced by multiple tools and vigilance.
For the next part, we will recommend tools to assess yourself and find out if your identity has been compromised.
Alternatively, if you want to skip ahead you will learn what to do if your identity has been stolen, with the last part of the series.

